Sniffit and libsnif are based on libpcap.
Usages
You can launch Sniffit without parameters and it will run using the default settings: lookup your network device and listen on port 80. But you can also specify the network device you want Sniffit open and a filtering expression.Sniffit uses Wireshark expressions to filter out, so you can provide expressions like "port 22", "host 192.168.1.100", icmp, ip, etc. Further expressions can be found at the Wireshark's wiki.
For example
Sniffing traffic on port 80 on the localhost
# ./sniffit -e "port 80"
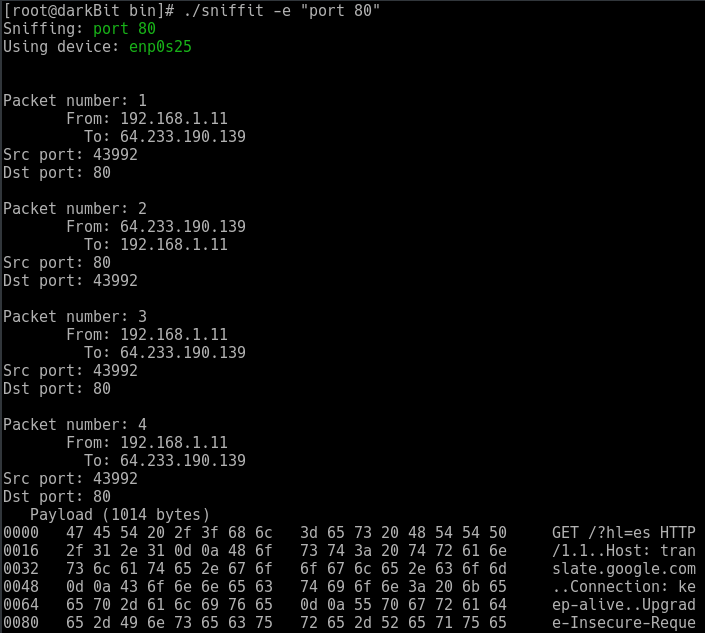
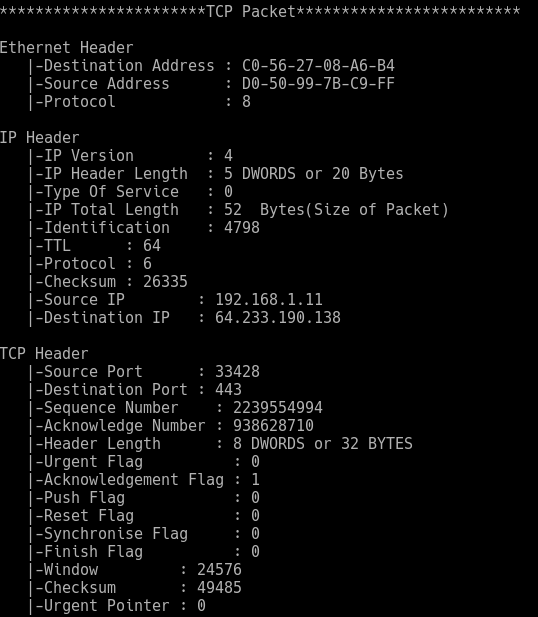
Since Sniffit opens your NIC in promiscuous mode, it needs root privileges to run.
Getting Sniffit
You can visit the GitLab page of the project, or you can get a snapshot dated on 2017-03-19.
Note that Sniffit is based on libpcap, so you need to install this dependency.
No comments:
Post a Comment